Hello, in this particular article you will provide several interesting pictures of us working on next steps to secure. We found many exciting and extraordinary us working on next steps to secure pictures that can be tips, input and information intended for you. In addition to be able to the us working on next steps to secure main picture, we also collect some other related images. Find typically the latest and best us working on next steps to secure images here that many of us get selected from plenty of other images.
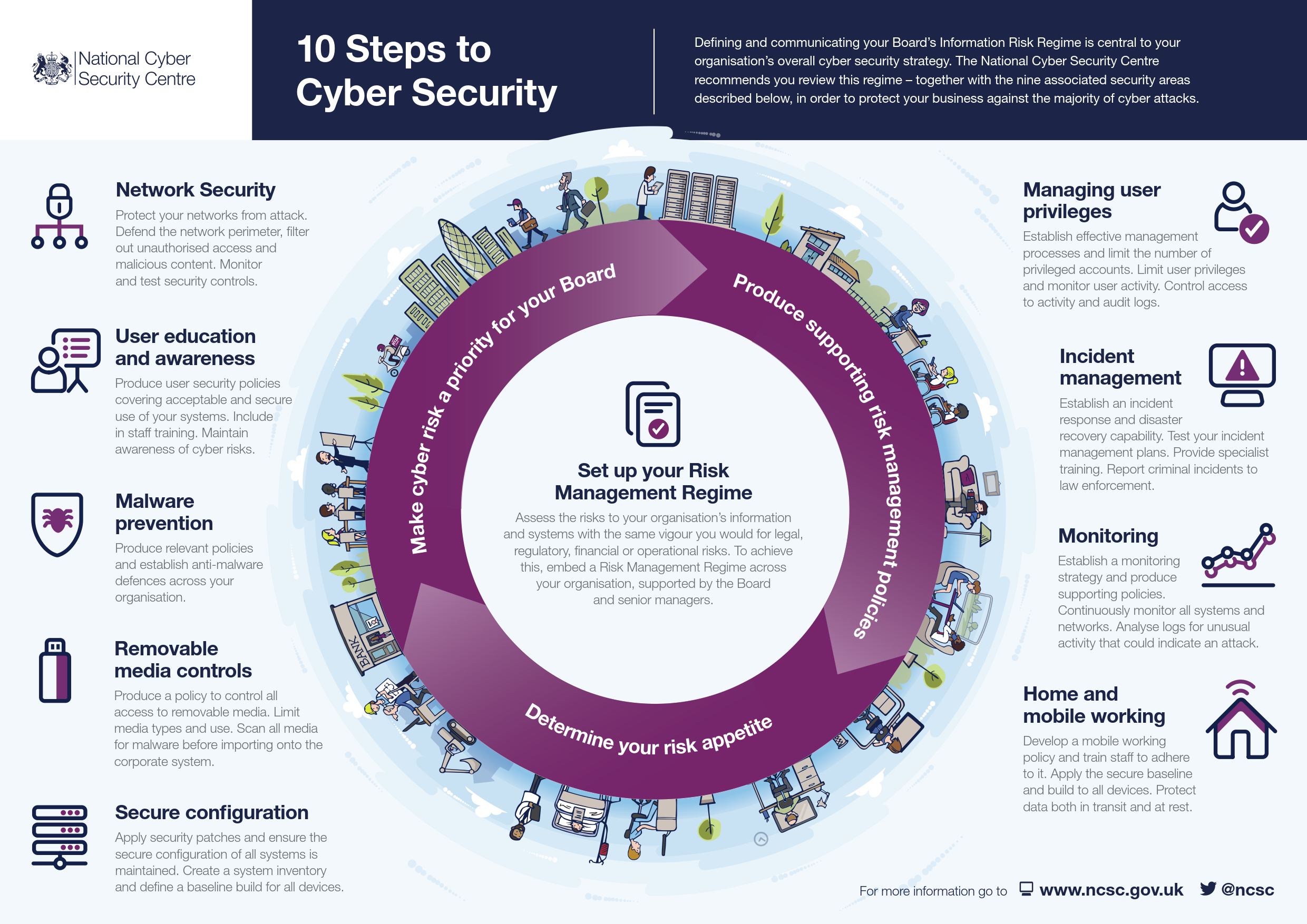 Infographic: Ten steps to cyber security - SAFETY4SEA We all hope you can get actually looking for concerning us working on next steps to secure here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
Infographic: Ten steps to cyber security - SAFETY4SEA We all hope you can get actually looking for concerning us working on next steps to secure here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
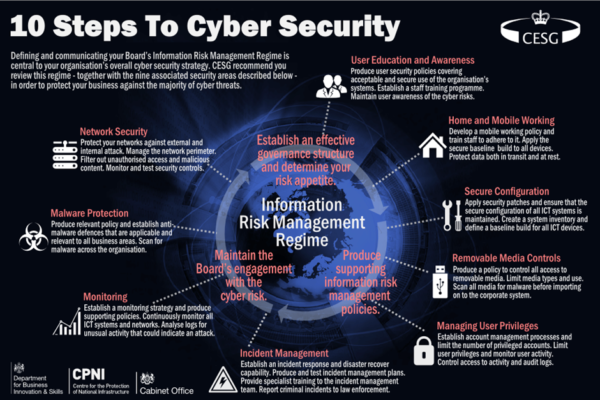 10-steps-to-cyber-security-infographic us working on next steps to secure - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the us working on next steps to secure image gallery that we all get prepared to locate the image you are interested in.
10-steps-to-cyber-security-infographic us working on next steps to secure - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the us working on next steps to secure image gallery that we all get prepared to locate the image you are interested in.
 5 Steps to Keep Your Information Secure | Cyber Security We all provide many pictures associated with us working on next steps to secure because our site is targeted on articles or articles relevant to us working on next steps to secure. Please check out our latest article upon the side if a person don't get the us working on next steps to secure picture you are looking regarding. There are various keywords related in order to and relevant to us working on next steps to secure below that you can surf our main page or even homepage.
5 Steps to Keep Your Information Secure | Cyber Security We all provide many pictures associated with us working on next steps to secure because our site is targeted on articles or articles relevant to us working on next steps to secure. Please check out our latest article upon the side if a person don't get the us working on next steps to secure picture you are looking regarding. There are various keywords related in order to and relevant to us working on next steps to secure below that you can surf our main page or even homepage.
 8 Steps to Cyber Security | Cyber Essentials | M-Tech Systems Hopefully you discover the image you happen to be looking for and all of us hope you want the us working on next steps to secure images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.
8 Steps to Cyber Security | Cyber Essentials | M-Tech Systems Hopefully you discover the image you happen to be looking for and all of us hope you want the us working on next steps to secure images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.
 17 Best Practices to Attain Secure Remote Work Environments | dinCloud All us working on next steps to secure images that we provide in this article are usually sourced from the net, so if you get images with copyright concerns, please send your record on the contact webpage. Likewise with problematic or perhaps damaged image links or perhaps images that don't seem, then you could report this also. We certainly have provided a type for you to fill in.
17 Best Practices to Attain Secure Remote Work Environments | dinCloud All us working on next steps to secure images that we provide in this article are usually sourced from the net, so if you get images with copyright concerns, please send your record on the contact webpage. Likewise with problematic or perhaps damaged image links or perhaps images that don't seem, then you could report this also. We certainly have provided a type for you to fill in.
 4 Easy Steps to Keep You Secure - TASK Virtual Assistant, LLC The pictures related to be able to us working on next steps to secure in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
4 Easy Steps to Keep You Secure - TASK Virtual Assistant, LLC The pictures related to be able to us working on next steps to secure in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
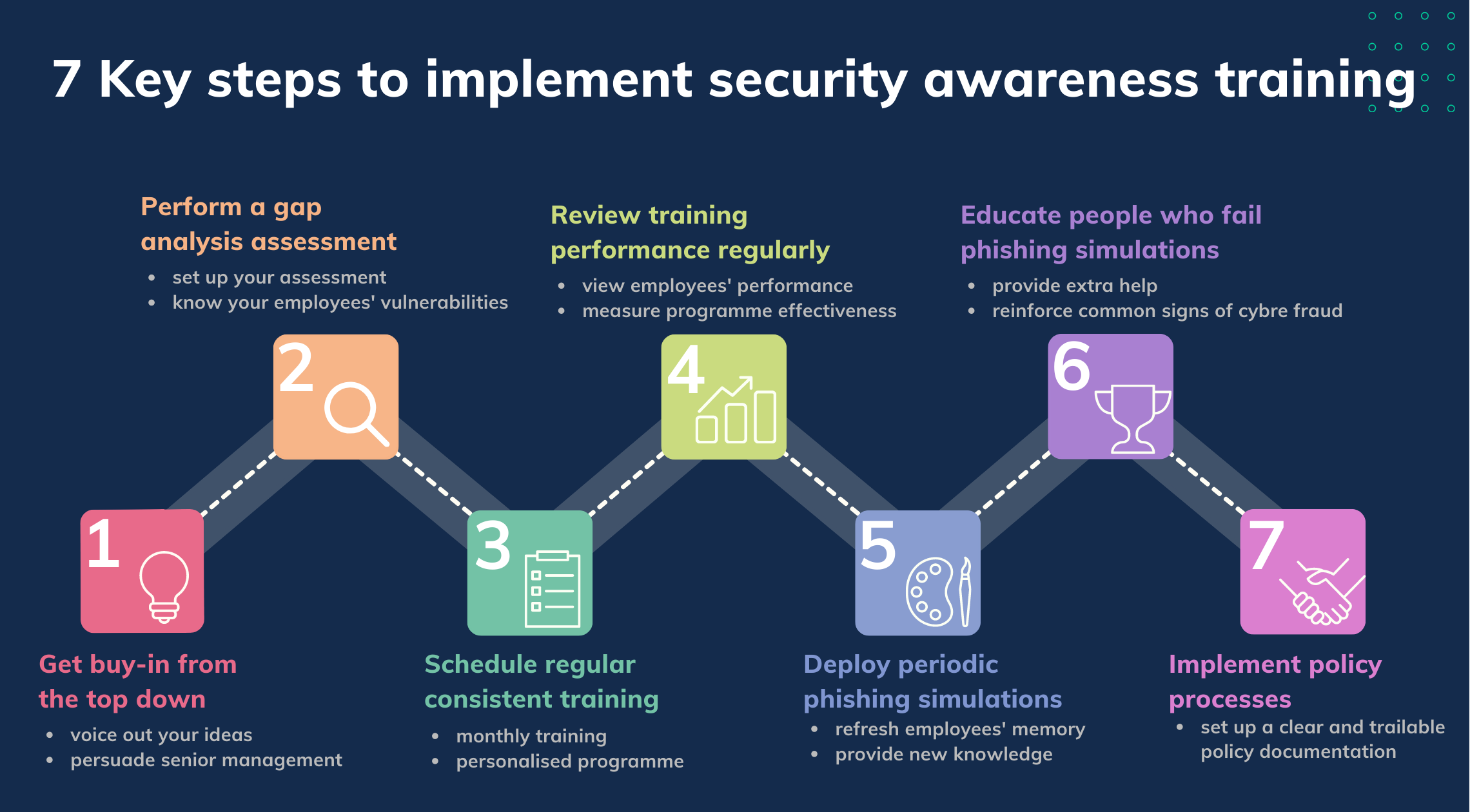 7 Key steps to implement security awareness training 7 Key steps to implement security awareness training
7 Key steps to implement security awareness training 7 Key steps to implement security awareness training
 Blog | Steps to Formulate Secure Remote Work Strategy Blog | Steps to Formulate Secure Remote Work Strategy
Blog | Steps to Formulate Secure Remote Work Strategy Blog | Steps to Formulate Secure Remote Work Strategy
 Five Steps to Security Resilience - MeriTalk Five Steps to Security Resilience - MeriTalk
Five Steps to Security Resilience - MeriTalk Five Steps to Security Resilience - MeriTalk
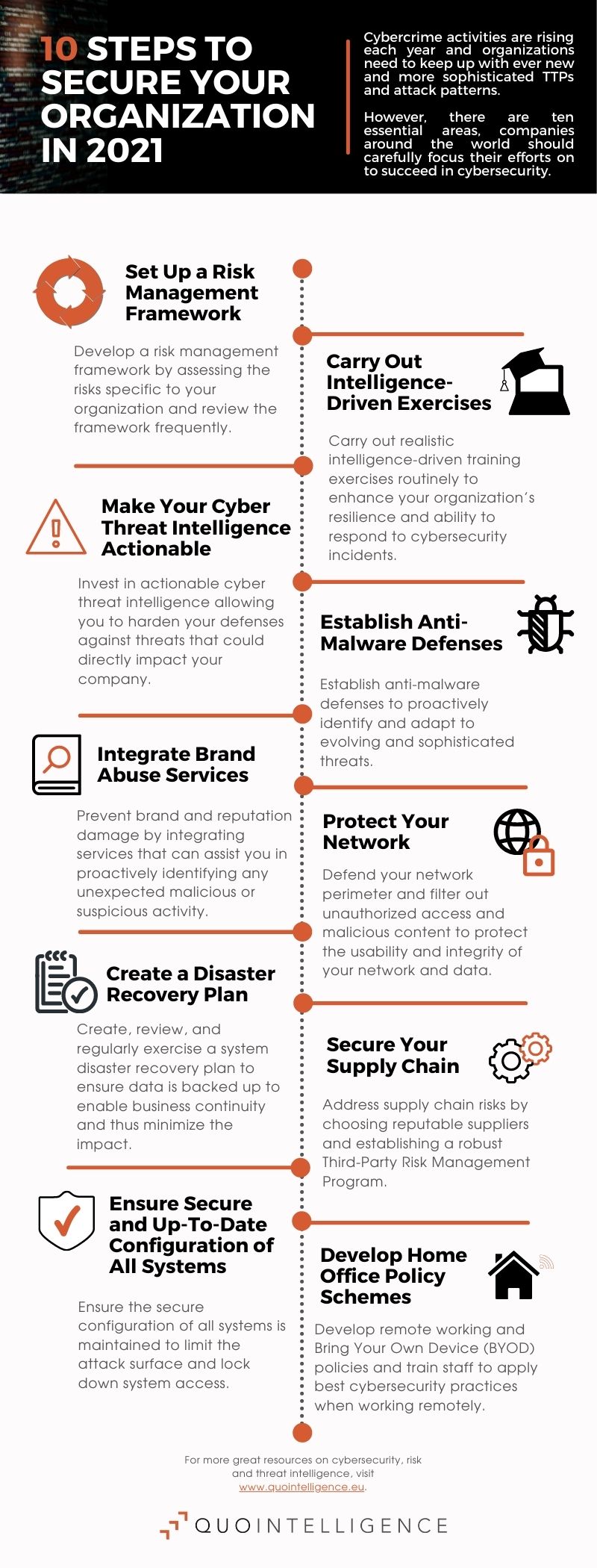 10 Steps To Secure Your Organization Against Cybercrime 10 Steps To Secure Your Organization Against Cybercrime
10 Steps To Secure Your Organization Against Cybercrime 10 Steps To Secure Your Organization Against Cybercrime
 Working Remotely? | Stronger International Inc | Cyber Security Working Remotely? | Stronger International Inc | Cyber Security
Working Remotely? | Stronger International Inc | Cyber Security Working Remotely? | Stronger International Inc | Cyber Security
 Cybersecurity Order of Operations (9 steps to security maturity) Cybersecurity Order of Operations (9 steps to security maturity)
Cybersecurity Order of Operations (9 steps to security maturity) Cybersecurity Order of Operations (9 steps to security maturity)
 Staying COVID-19 Secure 5 Steps to working safer together from Safety Staying COVID-19 Secure 5 Steps to working safer together from Safety
Staying COVID-19 Secure 5 Steps to working safer together from Safety Staying COVID-19 Secure 5 Steps to working safer together from Safety
 3 Steps To Becoming Cyber Secure 3 Steps To Becoming Cyber Secure
3 Steps To Becoming Cyber Secure 3 Steps To Becoming Cyber Secure
 4 Important Steps to Secure Web3 - US Today News 4 Important Steps to Secure Web3 - US Today News
4 Important Steps to Secure Web3 - US Today News 4 Important Steps to Secure Web3 - US Today News
 7 Key steps to implement security awareness training 7 Key steps to implement security awareness training
7 Key steps to implement security awareness training 7 Key steps to implement security awareness training
 4 Steps to Ensuring a Safe and Secure Workplace 4 Steps to Ensuring a Safe and Secure Workplace
4 Steps to Ensuring a Safe and Secure Workplace 4 Steps to Ensuring a Safe and Secure Workplace
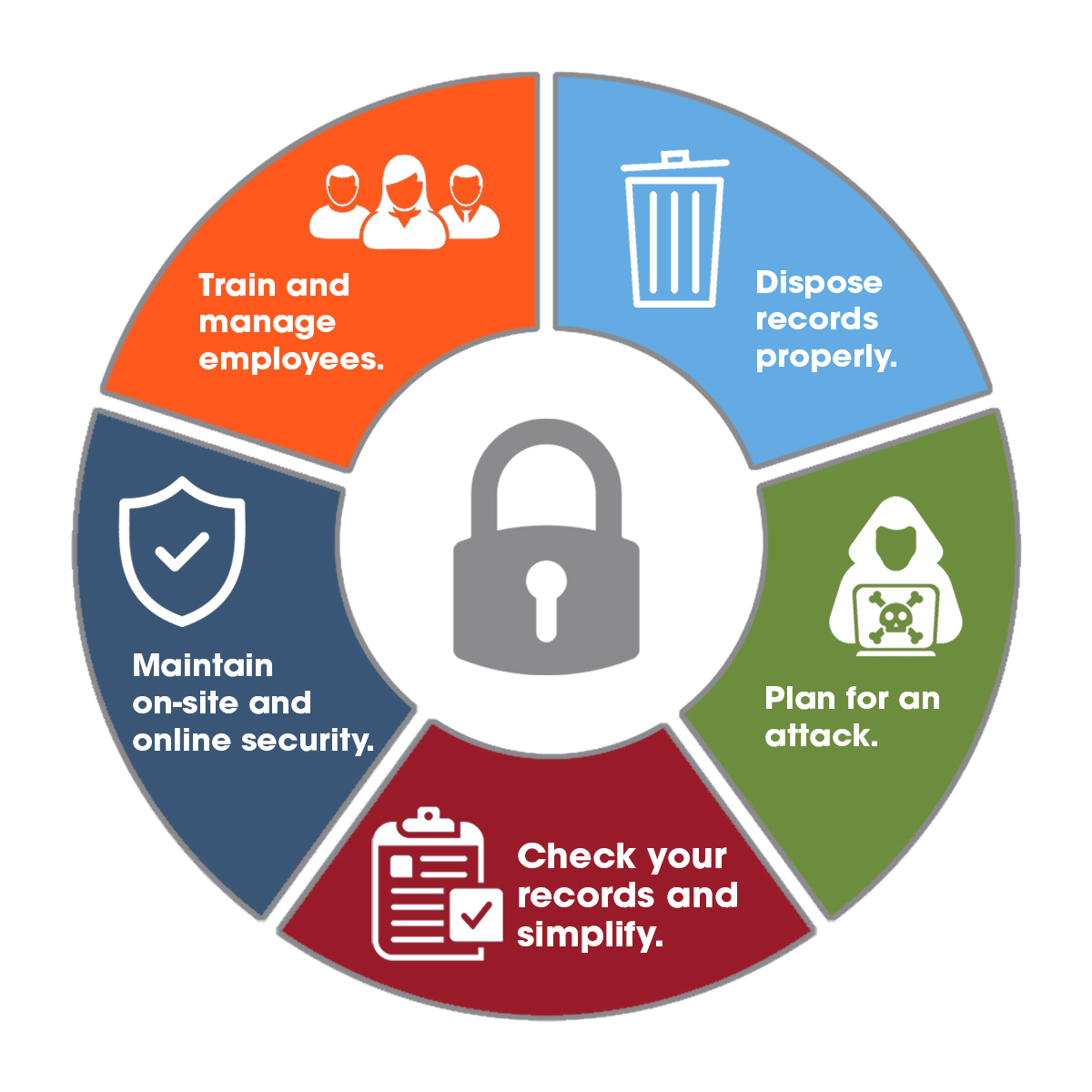 Information Protection Information Protection
Information Protection Information Protection
 Four Steps Toward a More Secure Network - Business Technology, Gadgets Four Steps Toward a More Secure Network - Business Technology, Gadgets
Four Steps Toward a More Secure Network - Business Technology, Gadgets Four Steps Toward a More Secure Network - Business Technology, Gadgets
 Get '8 Steps to Better Security: A Simple Cyber Resilience Guide for Get '8 Steps to Better Security: A Simple Cyber Resilience Guide for
Get '8 Steps to Better Security: A Simple Cyber Resilience Guide for Get '8 Steps to Better Security: A Simple Cyber Resilience Guide for
 5 Steps to Find and Eliminate Security Vulnerabilities - Working Security 5 Steps to Find and Eliminate Security Vulnerabilities - Working Security
5 Steps to Find and Eliminate Security Vulnerabilities - Working Security 5 Steps to Find and Eliminate Security Vulnerabilities - Working Security
 Cyber Security Degrees Cyber Security Degrees
Cyber Security Degrees Cyber Security Degrees
 3 Steps To Secure Your Company's WFH Culture 3 Steps To Secure Your Company's WFH Culture
3 Steps To Secure Your Company's WFH Culture 3 Steps To Secure Your Company's WFH Culture
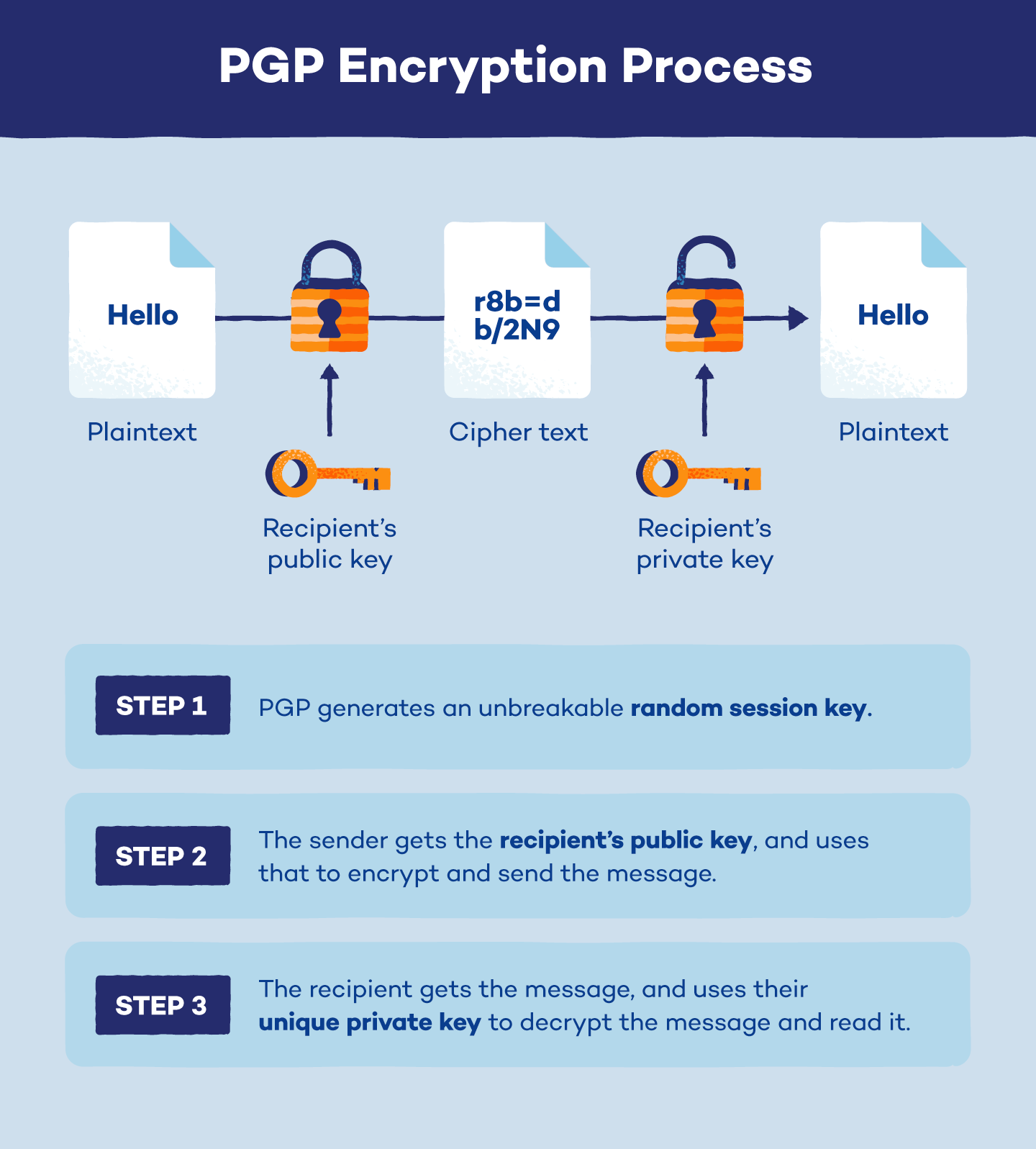 PGP Encryption: The Email Security Standard - Panda Security PGP Encryption: The Email Security Standard - Panda Security
PGP Encryption: The Email Security Standard - Panda Security PGP Encryption: The Email Security Standard - Panda Security
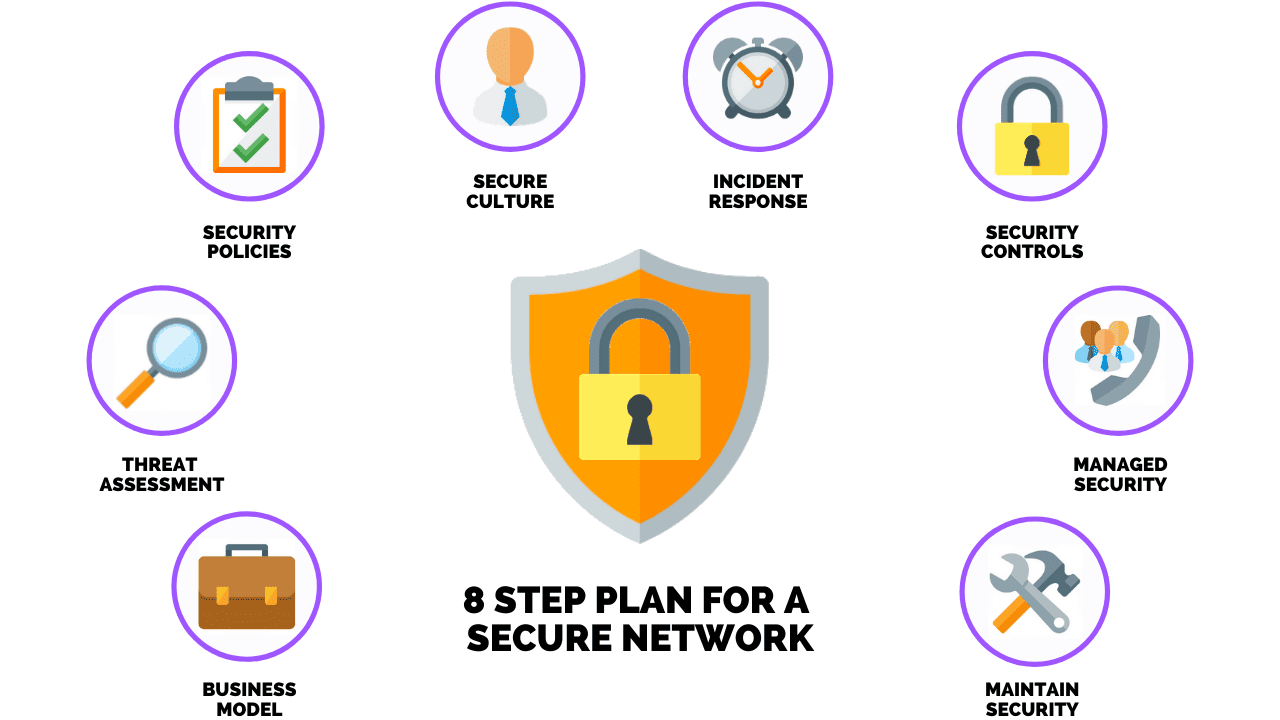 How To Develop & Implement A Network Security Plan How To Develop & Implement A Network Security Plan
How To Develop & Implement A Network Security Plan How To Develop & Implement A Network Security Plan
 Keep Your Sensitive Data Secure in 2020 with These 5 Steps! Keep Your Sensitive Data Secure in 2020 with These 5 Steps!
Keep Your Sensitive Data Secure in 2020 with These 5 Steps! Keep Your Sensitive Data Secure in 2020 with These 5 Steps!
 3 Simple Steps to Secure your Home or Business 3 Simple Steps to Secure your Home or Business
3 Simple Steps to Secure your Home or Business 3 Simple Steps to Secure your Home or Business
 Security Awareness Training - The Benefits and Why It Is Important Security Awareness Training - The Benefits and Why It Is Important
Security Awareness Training - The Benefits and Why It Is Important Security Awareness Training - The Benefits and Why It Is Important
 Career Advice: 13 Steps To Help Secure Your Job | Ivy Exec Career Advice: 13 Steps To Help Secure Your Job | Ivy Exec
Career Advice: 13 Steps To Help Secure Your Job | Ivy Exec Career Advice: 13 Steps To Help Secure Your Job | Ivy Exec
 Five Steps to Security: Best Practices Five Steps to Security: Best Practices
Five Steps to Security: Best Practices Five Steps to Security: Best Practices

